This afternoon, “Rebekah Jones” was trending on Twitter. A quick check revealed that her account was suspended by Twitter. Highly polarized tweets cheered her suspension and called her a fraud; even Florida Governor Ron DeSantis’ office chimed in. “Governor Ron DeSantis’s press secretary Christina Pushaw alleged that Jones was not suspended for anything she posted to her account. ‘She was suspended because she broke a clear rule against buying followers (platform manipulation) and — all evidence points to this — hijacking the accounts of unsuspecting users to make them follow her,’ Pushaw wrote on Twitter.”
As a long time fraud researcher, that allegation didn’t sit right. That’s because you don’t need to hijack other users’ accounts and make them follow you. There are literal hordes of fake accounts controlled by bots that can be instructed to follow any account by the millions within minutes. If you google the term “buy twitter followers” you will find thousands of vendors offering services to help you do exactly that. This is a tried and true practice for cheaters, dating back at least 10 years. See: Fake Twitter Accounts Followers Are Multi Million Dollar Business So I asked the #OSINT (“open source intelligence”) community for help.
Within minutes Conspirador Norteño @conspirator0, a researcher specializing in documenting Twitter fraud, wrote back with concrete evidence, including how it was done. The chart below (in yellow box) shows there was clearly a concentrated surge in new follower activity for @georebekah (red highlight on right edge). What is not known is whether Rebekah Jones purchased the followers herself, or whether it was a false-flag campaign meant to discredit her (someone else purchased the followers and directed them at her account to make it appear she broke Twitter’s rules).
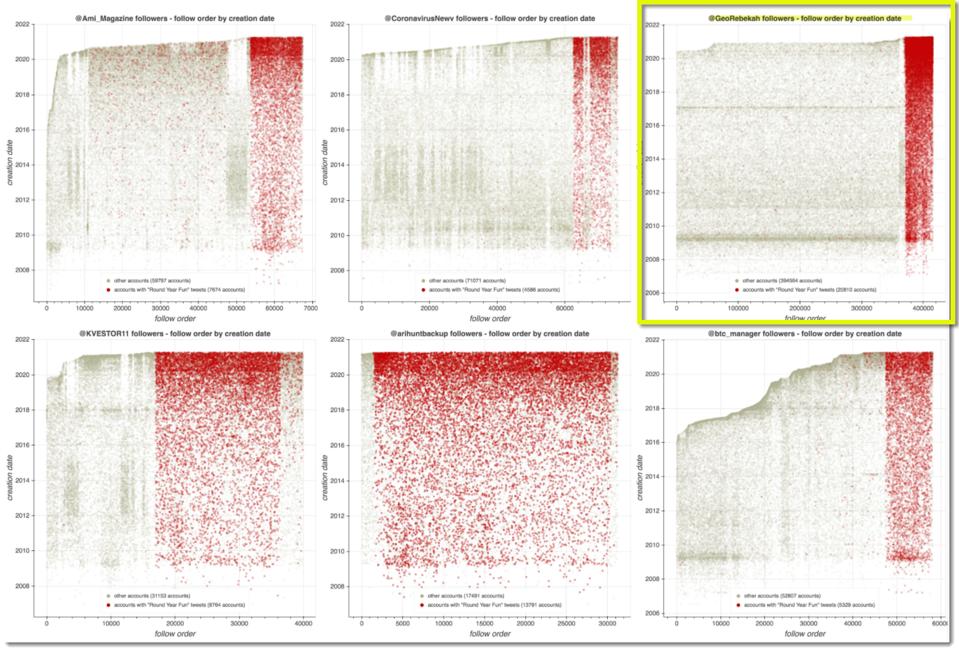
follower graphs over time
Nearly 21,000 followers were added in a short amount of time. This appeared to be the work of a family of apps called “Round Year Fun.”
@conspirator0 told me these apps, among many others, tricked real users into giving them account access permissions to their Twitter accounts so it could do silly things like plot the user’s friends in a circle. Typically those permissions included the ability to follow other accounts; and typically users forget to uninstall the malicious app or revoke account access and control permissions after getting the circle of friends chart. That’s when the malicious apps go to work.
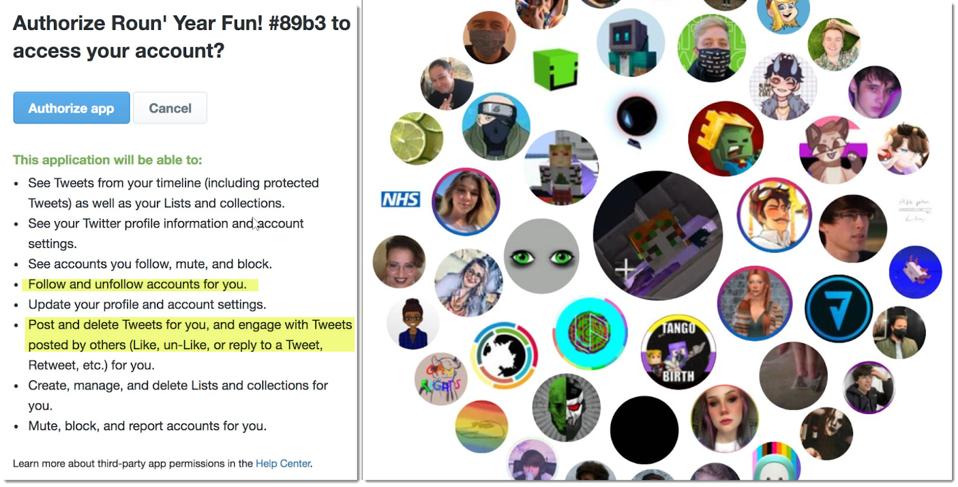
sample permissions and "circle of friends" chart
When someone buys Twitter followers from any number of vendors selling “real active Twitter account followers” for a premium, the network of apps springs into action to deliver exactly the number of followers that were purchased. The exact same methods are used to boost Instagram, TikTok, Facebook, and follower counts on other social media platforms. The scale of these fraud operations is massive too. @conspirator0 writes “How many accounts have been affected by Round Year Fun? We downloaded the latest 10 days' worth of tweets linking yearround(dot)fun, yielding 214,830 tweets from 180,402 accounts. The tweets were sent via 1,091 distinct apps, most with names that are variations on "Round Year Fun.”
All of the above was confirmed and documented in detail by another Twitter fraud researcher, Geoff Golberg, CEO of Social Forensics.
PSA for Twitter Users - Review Account Access Settings
As a public service announcement for Twitter users, be sure to check the “security and account access” section of your settings, review the apps that have permission to access and manage your account, and revoke permissions for apps you don’t recognize, look shady, or never use. Also, be sure to uninstall them from your phone too, since their presence means further cybersecurity risks beyond hijacking your Twitter account.
In the greater context of digital ad fraud, the techniques mentioned above are just a few of the tools in hackers and fraudsters' arsenals. If you think of a pyramid of sophistication, the lowest portion of the pyramid, the largest, consists of the simplest bots from data centers. These are headless browsers (real browsers, but without anything to display on screen). Such bots are used to repeatedly load webpages to generate enormous quantities of fake ads to sell through ad exchanges. The middle part of the pyramid consists of more advanced bots — e.g. malware or malicious apps that live on real humans’ devices. Their favorite environment is mobile, because gullible humans accidentally give permissions without reading carefully and the ecosystem of malware detection and prevention is far less mature in mobile environments. Once the malicious apps are downloaded onto the mobile devices, they can continuously load ads in the background to make money. Most humans don’t turn off their smart phones, even at night when they are sleeping. The devices have continuous access to the internet, which means fraud apps can make money 24/7, unlike on laptops and PCs which humans turn off at night. The tip of the pyramid consists of the advanced malicious apps that can fake touch events, page scrolling, or other human interaction events. Some bad apps might even record the real human users’ interactions and replay them to defeat more advanced fraud detection.
So What?
The simple lesson marketers should learn from this story is that fraudsters and bad actors have many tools at their disposal. While a handful of fraud cases get discovered, once in a while, most of the fraud remains hidden, so the perpetrators can continue making money. Because all of this takes place in the digital realm, the fraud schemes are highly scalable and highly profitable — whether it is selling involuntary Twitter follows or 100’s of billions of fake ad impressions.